Install tooling in Your Running System
The goal here is to prepare your environment to run the examples provided in TPM Pills, if (like me) you only trust what you see with your own eyes. It’s not a requirement. Indeed, you can limit yourself to read the content and code snippets. However, I strongly recommend you to read and run the examples to better understand the concepts.
Disclaimer regarding Windows
So far, my experience with TPMs has been exclusively limited to a Linux context — this is why, I am open to feedback from Windows users, if they encounter any issues.
Unfortunately, according to this issue, TPM is not added to WSL (Windows Subsystem for Linux), so it will be necessary to run commands from the host machine.
Prerequisites
TPM Pills will require you to have the following tools (in addition to git):
| Tool | Description | Linux Support | Windows Support | MacOS Support |
|---|---|---|---|---|
go >= v1.22 | A language that no longer needs an introduction | ✅ | ✅ | ✅ |
| openssl | Crypto Swiss Army Knife which here is a dependency for using the Software TPM | ✅ | ✅ | ✅ |
| swtpm | A Software TPM Emulator | ✅ | ✅ (using Cygwin) | ✅ |
| tpm2-tools | A CLI (Command-Line Interface) for interacting with a TPM | ✅ | ❌ | ❌ |
Table: Tooling support per Operating System
tpm2-tools is a great tool to have in your toolbox! However, since it is not available everywhere, it will be used sparingly.
Note:
PowerShellprovides some commands to interact with a TPM, but they will not be covered here.
Why go?
Most educational content on the subject is in C… but why follow the crowd, right?!
More seriously:
- I am not an experienced C developer, but I am proficient in Go
go-tpmprovides a rich interface for communicating with a TPM- In the upcoming pills, we will make the TPM interact with a server in gRPC, and Go allows me to do this easily
- More and more projects in Golang ecosystem use TPMs (e.g., spire, sks, u-root, constellation, etc.)
Fundamentally, since the TPM 2.0 interface is a standard, all the concepts we will cover here are also applicable in other languages.
TPM 2.0 Clients
For those interested, here is a (probably non-exhaustive) list of TPM 2.0 clients.
| Name | Language | Description |
|---|---|---|
| tpm2-tss | C | Intel implementation of TCG’s TPM Software Stack (TSS). The current standard meter bar regarding TPM libraries. |
| ibmtss | C | IBM implementation of TPM Software Stack (TSS) but not API compatible with TCG TSS. |
| wolfTPM | C | TPM 2.0 librairy designed for embedded system. |
| go-tpm | golang | |
| tpm2-pytss | python | Wrapper of tpm2-tss. |
| tpm-rs | rust | |
| rust-tss-fapi | rust | Wrapper of libtss2-fapi which is an upper API provided by tpm2-tss named FAPI1. Warning: project’s maintainers underline that the implementation is experimental and shouldn’t be use in production. |
| TSS.MSR | c#, c++, java, nodejs and python |
Table: TPM libraries
Installation
OCI
🚧 TBD 🚧
Nix
If you are a Nix user, TPM Pills provides a Nix shell (i.e. shell.nix) at the root of the repository.
To install dependencies, simply run the following commands:
git clone https://github.com/loicsikidi/tpm-pills.git
cd ./tpm-pills
# launch the derministic shell
nix-shell
# inside the shell
go version
tpm2 --version
Note: with this method
tpm2-toolswill only be installed on a Linux platform.
Devbox
For those who are unfamiliar, Devbox is a layer on top of Nix that allows you to obtain a deterministic shell without having to master the Nix language.
If you are a Devbox user, TPM Pills also provides a configuration (i.e. devbox.json) at the root of the repository.
To install dependencies, simply run the following commands:
git clone https://github.com/loicsikidi/tpm-pills.git
cd ./tpm-pills
# launch the derministic shell
devbox shell
# inside the shell
go version
tpm2 --version
Note: with this method
tpm2-toolswill only be installed on a Linux platform.
Manually
- go: Use your preferred package manager or download the binary from the official website
- openssl: Use your preferred package manager or get the sources from the official website
- swtpm: Use your preferred package manager or build the sources by following the official documentation
- tpm2-tools: Use your preferred package manager or build the sources by following the official documentation
Example: validate TPM’s version
Let’s finally get to the serious stuff! We will check the version of the TPM installed on your machine and ensure that it is a TPM 2.0. We will be able to do this by interacting directly with the TPM using a command called TPM2_GetCapability.
On Linux, access to the Hardware TPM is secured by sudo rights. It is possible to have finer control using a udev policy to allow specific users or groups to access it (e.g., the policy available in NixOS).
tpm2-tools
Only works on Linux.
# dependending on your config it might require 'sudo'
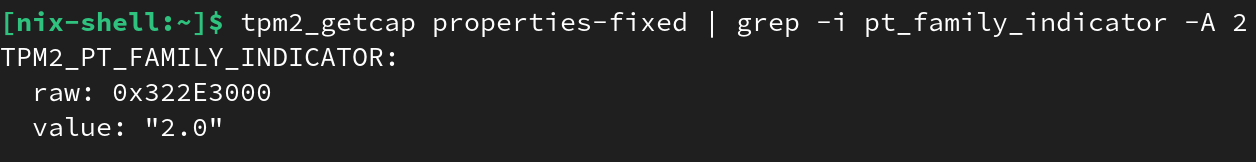
tpm2_getcap properties-fixed | grep -i pt_family_indicator -A 2
You should get the following output:
go
The script will works on all environments (on Darwin, the code relies on a Software TPM).
Run the following command:
# dependending on your config it might require 'sudo'
go run github.com/loicsikidi/tpm-pills/examples/02-pill
# output:
# TPM Version: 2.0
Depending on your local setup, you can also run the following command:
# nix command
nix-shell --run "go run github.com/loicsikidi/tpm-pills/examples/02-pill"
# devox command
devbox run -- go run github.com/loicsikidi/tpm-pills/examples/02-pill
Next pill…
…we will see in much more details how we can interact with a TPM.
🚧 TPM Pills is in beta 🚧
- if you encounter problems 🙏 please report them on the tpm-pills issue tracker
- if you think that
TPM Pillsshould cover a specific topic which isn’t in the roadmap, let’s initiate a discussion 💬
-
Feature API ↩